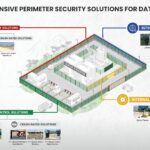
When Threats Change, So Should Your Security Strategy

Why Industry-Specific Perimeter Security Is the Future
In an era where threats are constantly shifting, from drones to data breaches, security cannot remain static. Critical infrastructure sectors like Oil & Gas, Power Generation, and Data Centers face unique, evolving risks. Applying the same security blueprint across such vastly different industries is not only ineffective but also dangerous. Each facility requires a tailored perimeter security fence solution that reflects its specific vulnerabilities, site layout, and operational environment.
At A-1 Fence, we believe that effective perimeter security should be as dynamic as the threats it is built to counter. This blog dives into key industry-specific threats and demonstrates how our tailored solutions help build smarter, more resilient perimeters. Learn how choosing the right perimeter security fence plays a critical role in defending against modern, multi-dimensional threats.
Oil & Gas: Remote Sites, Explosive Risks, and Surveillance Challenges
THREAT 1: Remote Intrusion & Theft
Oil & gas sites are often isolated and cover vast land. This makes them prime targets for organized theft, illegal tapping, or unauthorized access. Robust security fencing for oil and gas applications, including oil & gas perimeter fencing, ensures early detection and deterrence across remote and high-risk assets.
How A-1 Secures It:
- Delay-Rated Fence Systems like A-1 AKAT® add crucial time in case of a breach, allowing intervention before sabotage or vandalism escalates.
- A-1 Welded Mesh Fence Systems with anti-climb design and razor wire toppings create strong visual and physical deterrents.
- Liminal-F (our advanced PIDS) is embedded along the perimeter to detect climbing or cutting attempts in real time, providing early alerts even before intruders fully breach.
- Thermal & CCTV Surveillance Integration enables 24/7 monitoring, even in low visibility.
THREAT 2: Drone Intrusion
Drones can survey, drop payloads, or hack wireless signals. Traditional ground-focused perimeters can’t protect from above. An anti drone fence, when paired with aerial threat detection systems, fortifies airspace and defends critical infrastructure against overhead surveillance or payload threats.
How A-1 Secures It:
- Radar-Based Drone Detection Systems combined with perimeter alarms create a 3D detection bubble.
- Anti-Drone Fence stops drones from entering the site
Power Plants: Sabotage, Protestors, and Redundancy Risks
THREAT 3: Targeted Sabotage or Vandalism
Power plants are prime targets for disruptive actors. Even a short disruption can trigger widespread outages. Installing a purpose-built generating station fence helps mitigate physical threats and ensures operational continuity at high-priority energy production sites.
How A-1 Secures It:
- Delay-Rated Weldmesh Fencing makes forced entry time-consuming and resource-intensive.
- Boom Barriers and Hostile Vehicle Mitigation (HVM) Bollards prevent ramming attacks at entry points.
- 3rd party Integrated Video Surveillance and Access Control ensure only vetted personnel can enter sensitive areas.
THREAT 4: Civil Unrest and Crowd Intrusion
Public protests near power facilities can quickly escalate, making perimeter control essential. Deploying a reinforced perimeter security fence during times of unrest ensures crowd management and infrastructure protection under pressure.
How A-1 Secures It:
- Crash-Rated Fencing and Modular Barricade Systems help secure outer perimeters during high-alert scenarios.
- Temporary but Sturdy Fencing Panels allow quick deployment and controlled channeling of crowds.
THREAT 5: Fire Risk and Equipment Tampering
Open transformers and cables are often exposed to arson or casual vandalism.
How A-1 Secures It:
- Liminal-F and Liminal-K detect vibrations or digging attempts near underground cables or fence posts.
Data Centers: The New Battleground of Physical + Digital Security
THREAT 6: Insider Access & Social Engineering Breaches
Hackers often use physical intrusion as the first step to cybercrime. They may impersonate staff or exploit weak physical access points.
How A-1 Secures It:
- Biometric Turnstiles and Smart Gates (A-1 Entranso Series) tightly regulate access, no more tailgating or stolen swipe cards.
- Integration with access logs + CCTVs + AI analytics helps flag suspicious entry patterns.
THREAT 7: Perimeter Blind Spots
High-value data centers are often located in urban environments where nearby structures create surveillance blind spots. Smart electric fencing for data centers enhances real-time detection, while comprehensive data center perimeter security reduces the risk of stealthy intrusions.
How A-1 Secures It:
- 360° AI Radar Surveillance Systems mounted along high fences provide behavior-based alerts (e.g., loitering, unusual motion).
- Advanced Anti-Climb Fencing reduces the risk of scaling, especially in blind zones.
THREAT 8: Coordinated Cyber-Physical Attacks
An intruder breaches the fence just as a digital denial-of-service attack begins. Physical perimeter protection must align with IT.
How A-1 Secures It:
- Our solutions are physically ready, meaning our perimeter detection (Liminal Series) integrates into central command systems.
- This allows real-time response orchestration between IT and physical security teams.
The Bottom Line: No Two Threat Profiles Are the Same
Using the same security strategy for an oil rig and a data center is like using the same lock for your front door and your bank vault. It’s ineffective and risky.
Instead, A-1 Fence designs perimeter security systems based on:
- Site location and terrain
- Threat likelihood and intensity
- Redundancy and response time requirements
- Industry-specific compliance and operational needs
We don’t just sell fences, we build resilience into your perimeter.
Your threats have evolved, have you perimeter? In today’s landscape, real security lies in designing intelligent, adaptive strategies tailored to your industry. From rugged oil rigs to sophisticated data hubs, we secure what matters by thinking beyond the fence.
A-1 Fence has secured critical infrastructure in over 50 countries with perimeter solutions tailored to the most demanding environments. Our clients include global oil conglomerates, government power utilities, hyperscale data centers, and more.
Ready to Future-Proof Your Perimeter?
Let our experts help you reimagine security, from the ground up.
👉 Contact Us
Stay Ahead of Evolving Threats.
Follow A-1 Fence on LinkedIn for expert insights, new tech updates, and field-tested strategies.