Designing Resilient Perimeters: Moving Beyond Walls to Strategic Defense
In today’s world, threats don’t knock, they strike.
Perimeter security is no longer just about building higher walls or hiring more guards. From drones and sabotage to coordinated intrusion attempts, modern threats are dynamic, persistent, and often unpredictable. Strategic perimeter fencing solutions now integrate intelligence, layering, and rapid‑response readiness.
A single breach, even if momentary, can set off a chain of serious consequences. From operational disruptions that halt critical infrastructure to financial losses due to theft or damage, the impact can be immediate and far-reaching. Reputational harm often follows, undermining stakeholder trust and regulatory confidence. In high-risk zones like oil terminals, prisons, or military sites, such intrusions can even cost lives. Integrating perimeter fencing solutions with a perimeter surveillance radar system helps detect threats early, containing risks before they escalate across critical infrastructure zones.
In this blog, we explore how leading facilities are moving beyond traditional barriers to build truly resilient perimeters. You’ll learn how to design a multi-layered defense using the 3 Ds—Deterrence, Detection, and Delay, across outer, mid, and inner zones. With real-world examples and actionable insights, this post will help you rethink perimeter security as an intelligent, adaptable system fit for today’s evolving threats.
So, how do you protect a critical asset in such a world?
You build resilience, not just barriers.
What is Perimeter Resilience?
Perimeter resilience is the ability of a security system to anticipate, withstand, adapt to, and recover from potential threats. It goes beyond just building boundaries but incorporates a strategy that is capable of foreseeing potential threats and vulnerabilities to the perimeter, resisting attacks without being completely breached or having its core functions disrupted, learning from security incidents, and adapting perimeter defenses to improve its effectiveness against future threats. Robust perimeter fencing solutions, paired with a perimeter intrusion detection system India trusts, transform passive boundaries into adaptive, intelligence‑driven defense ecosystems.
How to build Perimeter Resilience?
Building perimeter resilience starts with identifying and analyzing how and where intrusions can happen. With the evolving modern threats, having a single solution approach is no longer sufficient. True resilience comes from a layered security strategy that integrates physical barriers, intrusion detection technologies, surveillance systems, and rapid response protocols.
At its core lies the 3 Ds of perimeter security:
- Deterrence
- Detection
- Delay
These three elements work in tandem to stop an intruder before they can cause harm. Let’s break this down:
1. Deterrence: Stop the threat before it begins
Deterrence is the first and most visible layer of defense. Its purpose is simple but powerful: to make an intruder think twice before attempting a breach. Through physical barriers like anti-climb fences, razor wire, lighting systems, and clear warning signage, deterrence creates psychological resistance. A well-deterred perimeter can stop many threats before they even begin. Effective perimeter fencing solutions reinforce these deterrents, projecting strength while minimising opportunities for opportunistic breaches.
Goal: Discourage unauthorized access through visible and psychological barriers.
Key deterrents include:
- Anti-climb fencing designs like spikes, curved tops, and weldmesh panels
- High-security fencing such as razor wire, palisade fences, or delay-rated barriers
A visually intimidating perimeter sends a strong message: this site is protected.
2. Detection: Know before it happens
Even the best deterrents can be bypassed, which is why detection is critical. Detection systems ensure you’re not just reacting to incidents, but anticipating them. Smart technologies like PIDS, fiber optic sensors, AI-powered CCTV, and radar surveillance help identify threats the moment they emerge. Early detection means faster response and reduced risk of escalation.
Goal: Instantly sense any breach attempt—before it escalates.
Smart detection tools:
- Perimeter Intrusion Detection Systems (PIDS) such as Liminal-F or RazorSense™
- Fiber optic sensors, vibration, or motion detectors
- AI-powered CCTV cameras with real-time analytics
- Thermal imaging for zero-visibility environments
These tools allow real-time threat identification, enabling rapid response and minimizing damage.
3. Delay: Buy time to respond
When an intruder breaches the perimeter, every second counts. Delay mechanisms are engineered to slow down unauthorized access, buying vital time for intervention. From delay-rated fences like A-1 Akat NG 30 to vehicle barriers and buffer zones, these solutions create friction at every stage of intrusion, turning a few seconds of vulnerability into minutes of managed response.
Goal: Slow down the threat to give responders time to act.
Effective delay mechanisms:
- Delay rated fences, such as A-1 Akat®, are capable of resisting high-power tools for 6–30 minutes
Vehicle barriers and bollards to halt ramming attacks - Buffer zones and layered fencing to force multiple breach attempts
- When seconds matter, these few extra minutes can make all the difference.
The Power of Layered Defense
A truly resilient perimeter doesn’t rely on a single fence or camera—it uses concentric layers of security:
| Layer | Function |
| Outer Layer | Deter and delay with fencing, signage, barriers |
| Mid Layer | Detect with sensors, CCTV, and surveillance tools |
| Inner Layer | Stop and neutralize with access control, guards, and alerts |
Each layer is tailored to the site’s terrain, threat profile, and criticality level, creating a customized defense ecosystem.
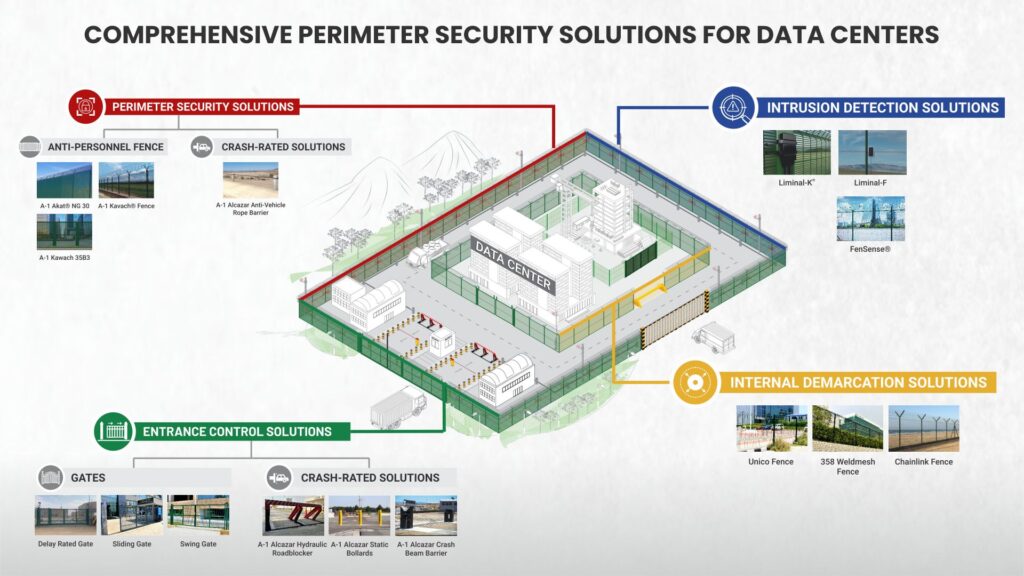
Example: Layered Perimeter Security for a Data Center
Imagine a Tier IV Data Center hosting mission-critical applications for global enterprises, government institutions, and cloud service providers. Even a few seconds of unauthorized access could result in massive data theft, service disruption, or regulatory violations. Protecting such a facility demands more than just strong walls—it requires a smart, multi-layered perimeter security strategy.
Let’s walk through how each layer works together to secure this high-risk digital fortress:
Outer Layer: Perimeter Security Solutions – Prevent Before Penetrate
The perimeter is secured using anti-personnel fencing like A-1 AKAT® NG 30 and A-1 Kavach® 3583, built to resist cutting, climbing, and power tool attacks. For vehicle threats—such as hostile trucks or ramming attempts—A-1 Alcazar Anti Vehicle Rope Barriers provide critical crash protection.
This layer acts as both a visual and physical deterrent, clearly signaling that the facility is monitored, fortified, and off-limits. It forms the first obstacle in stopping any unauthorized physical intrusion attempt before it reaches core operations.
Mid Layer: Intrusion Detection Solutions – Real-Time Intelligence
Next, smart detection systems are embedded into the perimeter fences. Liminal-K®, Liminal-F, and FenSense® continuously monitor the fence line using MEMS-based sensing, fiber optics, and real-time analytics. This perimeter intrusion detection system seamlessly scales with site growth, ensuring surveillance remains comprehensive and proactive.
Any attempt to tamper with, climb, or breach the fence triggers an immediate alert, allowing the security team to respond before the attacker gains further access. For a data center handling real-time financial or governmental systems, this detection layer is crucial for preventing latency-sensitive downtime or data compromise. A fence perimeter intrusion detection system pinpoints breach location instantly, enabling coordinated guard dispatch and minimal service disruption.
Inner Layer: Internal Demarcation – Zone-Based Containment
Inside the facility, secondary fences like Unico Fence, 358 Weldmesh, and Chainlink Fences create secure internal zones—for example, separating cooling systems, power distribution units, or server halls. These prevent lateral movement, contain insider threats, and ensure that even if an intrusion occurs, access to critical assets is further delayed and monitored.
This layered zoning ensures segmented protection, where each operational area is independently secured to reduce the blast radius in the event of a breach.
Controlled Entry: Entrance Solutions – Secure by Design
Entry and exit points are equipped with delay-rated gates, swing/sliding gates, and access control booths. For high-risk vehicular access, A-1 Alcazar Hydraulic Roadblockers, Static Bollards, and Crash Beam Barriers are installed, ensuring that no unauthorized vehicle can force entry.
This gate system allows for verified access control while remaining scalable for data center operations such as equipment delivery, generator servicing, and emergency maintenance. Facilities often specify automatic sliding entrance gates or an integrated automatic entrance gate to blend secure access with operational efficiency.
Outcome: A Resilient, Data-Centric Defense Ecosystem
Each layer—whether physical or intelligent—plays a key role in creating a resilient perimeter tailored to the operational realities of data centers. The combination of deterrence, detection, and delay ensures that any intrusion attempt is:
- Detected early
- Contained quickly
- Neutralized before it reaches sensitive IT infrastructure
By deploying this multi-layered approach, data centers can minimize downtime risk, ensure regulatory compliance, and protect the digital backbone of global businesses.
Designing a perimeter today isn’t just about keeping people out—it’s about designing a defense system that can think, respond, and adapt. By applying the 3 Ds—Deterrence, Detection, and Delay, and layering them based on threat levels and terrain, organizations can:
- Strengthen perimeter protection
- Minimize false alarms and maximize response time
- Create adaptable systems for evolving threats
At A-1 Fence, we’ve implemented perimeter security solutions across 50+ countries, protecting assets as diverse as energy plants, border outposts, data centers, and critical infrastructure. Our strength lies in designing perimeter systems that not only protect but intelligently defend.
From anti-intrusion fences to smart detection systems, every solution is tailored to the terrain, threat, and technology landscape.
Ready to Build Resilience?
Let A-1 Fence, our experts, help you design a customized, multi-layered perimeter defense strategy based on your site conditions and threat profile.
👉 Contact us to Start Your Perimeter Assessment
📲 Stay updated with security trends, innovations, and case studies— Follow A-1 Fence on LinkedIn





